2021-01-05: Summary of "BRON--Linking Attack Tactics, Techniques, and Patterns with Defensive Weaknesses, Vulnerabilities and Affected Platform Configurations"
 |
| Figure 1: Visualization of BRON with Vulnerabilities and Affected Product Configurations (Source: Hemberg et al.) |
Cyber threats, like the recent SolarWinds Sunburst attack, are harmful and hard to defend against. However, multiple sources of information about potential threats and vulnerabilities are publicly available to help. These kinds of sources are intended to be used by cyber security specialists and threat hunters to develop cyber defense strategies, operations, and tactics. The definitions of a few key terms will provide context for the research concepts discussed in this post.
- Tactic. A general, beginning-to-end strategy an adversary might use to gain access to valuable systems and information.
- Technique: Describes how an adversary achieves a tactical objective.
- Attack Pattern: A series of repeatable steps that can be applied to simulate an attack against the security of a system.
- Weakness: An error in software code that might lead to a vulnerability.
- Vulnerability: A weakness that can be exploited by an adversary.
Many public sources of cyber threat and vulnerability information exist to serve the defense of cyber systems. In their paper, "BRON--Linking Attack Tactics, Techniques, and Patterns with Defensive Weaknesses, Vulnerabilities and Affected Platform Configurations", Hemberg et al. propose an open-source, relational graphing tool, BRON, which links public threat data from MITRE's ATT&CK Matrix, Common Attack Pattern Enumeration and Classification (CAPEC), NIST’s Common Weakness Enumerations (CWE), and Common Vulnerabilities and Exposures (CVE). BRON preserves all entries and relations while enabling bi-directional, relational path tracing. It exploits attack patterns to trace between the objectives and means of attacks to the vulnerability. Hemberg et al. fuse the following data sets to create the relational graph, Figure 1, and facilitate ease of use.
- The MITRE ATT&CK matrix describes cyber attack Techniques organized across twelve sequenced cyber attack Tactics. One such Tactic is Persistence, occurring after Initial Access and before Privilege Escalation. ATT&CK lists T1098/004 as a Technique that achieves persistence.
- The CWE enumerations are a community-developed source of software and hardware weakness types. In the CWE, “Weaknesses are flaws, faults, bugs, and other errors in software and hardware design, architecture, code, or implementation that if left unaddressed could result in systems, networks, and hardware being vulnerable to attack.” CWE-269: Improper Privilege Management is an example CWE entry.
- The CVE list holds publicly known cybersecurity vulnerabilities. In the CVE, a vulnerability is defined as a “weakness in the computational logic (e.g., code) found in software and hardware components that, when exploited, results in a negative impact to confidentiality, integrity, or availability.” CVE-2019-12183 is a CVE Vulnerability described as “Incorrect Access Control in Safescan Timemoto TM-616 and TA-8000 series allows remote attackers to read any file via the administrative API."
- The CVE entry also provides a field with a severity score in Common Vulnerability Scoring System (CVSS) format and Affected Product Configurations (i.e., hardware, software) found in the Common Platform Enumeration (CPE). The affected software or hardware releases are of interest, because, with an inventory, security operators and analysts can regularly scan them to be alerted to specific targets within their systems.
This composite set of information enables both cyber-hunting and reactive, preventative and forensic security analysis on strategic, operational, and tactical levels. The CWE, CVE, and Affected Product Configurations inform where weaknesses and vulnerabilities exist in a system. Attack patterns link potential attack actions to weaknesses that would become attack targets.
BRON Implementation Overview
BRON is implemented as a relational graph which represents the entries of its different information sources as specific types of nodes and their internal and external linkages as edges. BRON offers path finding all the way from abstract attacker tactical goals, such as Persistence, down to the specific applications that can be targeted as part of an attack, or vice versa. The authors use BRON to collect products of a vendor by parsing the CPE notation for Affected Product Configurations which includes the vendor, product, and version. The data for Figure 2 are extracted by finding the number of products of each vendor that are vulnerable to each Tactic. Similarly, the data for Figure 3 are extracted by finding the number of versions of each vendor product that are vulnerable to each Tactic. Finally, the data for Figure 4 are extracted by finding the severity scores of products of each vendor. Products are referenced within Vulnerabilities that also have severity scores. Since a product may link to multiple vulnerabilities with each vulnerability having its own severity score, BRON takes the maximum severity score among the product’s set of vulnerabilities as that product’s severity score.
 |
| Figure 2: Heat map showing number of unique products by vendor that are exposed to nine Tactics. (Source: Hemberg et al.) |
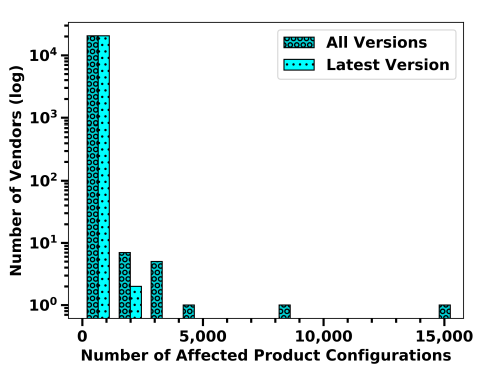 |
| Figure 3: Number of Affected Product Configurations for different vendors. (Source: Hemberg et al.) |
 |
| Figure 4: Distributions of severity scores for Affected Product Configurations connected to all Tactics. The scoring density by vendor is presented using a Violin Plot. (Source: Hemberg et al.) |
Analyses
Hemberg et al. used the data available from the information sources as of March 2020 and updated only the CVE data as of June 2020 to populate BRON. The analyses are organized by different lenses discussed below.
Entry and Relational Analyses
The first set of analyses determined the breadth and depth of the entries and relations within BRON. This involves counting BRON’s nodes and edges by type using different filters. The analyses are at different resolutions. First, they looked at BRON in the aggregate by investigating the relational connectivity, followed by considering each source individually. Finally, the authors considered severity scores. In Figure 1, we observe what the authors call Floating Entries, i.e. entries that are isolated or orphaned. Only a small fraction of Techniques are Floating Entries (1 of 266). By definition, no Weaknesses or Affected Product Configurations are Floating Entries. There are, however, two obvious sets of Floating Entries. Of the 71,715 Vulnerabilities, 28% are floating entries. Of the 519 Attack Patterns, 25% are Floating Entries. This draws attention to a level of incompletion within BRON as the underlying data sources are constantly being updated. Figure 1 also shows Super Entries which equate to specific entries that are the destination and/or source of many relational cross-references, i.e. nodes with many edges. The authors expect Super Entries given there are many more Vulnerabilities and Affected Product Configurations than other entry types. These naturally will be more densely inter-connected.
Vulnerability Paths
Hemberg et al. also consider paths connecting through Vulnerabilities, identifying them as Vulnerability Paths. Figure 5 shows yearly trends of how many such paths start from, respectively, a Tactic, an Attack Pattern, or a Weakness, and end at a Vulnerability. It also shows how many Vulnerabilities are not connected to a weakness. They surmise that over time, more Vulnerabilities are reported possibly due to more products in use and increased bug reporting by vendors.
CVSS and Vendor Severity Scores
The authors define BRON’s non-demonstrated severity as the sum of CVSS severity scores assigned to Vulnerabilities that are not yet linked to any Affected Product Configurations (i.e. specific products and versions). It contrasts with operational severity which is the sum of severity scores assigned to Vulnerabilities which have at least one Affected Product Configuration. Hemberg et al. define total severity as the sum of non-demonstrated and operational severity. Nearly 25% of non-demonstrated Vulnerabilities have severity scores of 0. This correlation between the number of Floating Entry Vulnerabilities and the number of low severity scores suggests that Vulnerabilities not linked to Weaknesses tend to have lower severity scores. The length of the tails for the different public threat data types, Figure 6, is interesting, as well. Hemberg et al. imply this might indicate a categorization error (i.e., should have more refined categories) or that some analysts spend more effort finding and writing out the vulnerabilities.
The authors also consider the severity of Vulnerabilities for a set of top-10 vendors. Figure 7 shows the distribution of severity scores of vendor products across all Tactics, collecting the maximum Vulnerability severity score of all versions. The distributions across vendors are significantly different. The severity score distribution for Affected Product Configurations connected to specific Tactics is sometimes different than severity score distribution for all Affected Product Configurations of a vendor. For each vendor, Hembeg et al. count the number of entries per source affecting them, given there are paths in BRON from Attack Patterns up to Techniques.
 |
| Figure 7: Number of entries per source for Top-10 vendors. (Source: Hemberg et al.) |
Example Queries
Given Persistence or any other Tactics, BRON can be used to retrieve the related Techniques, Attack Patterns connected to the Techniques, the Weaknesses connected to the Attack Patterns, the Weaknesses connected to the Vulnerabilities, the Affected Product Configurations listed within Vulnerabilities, and the Vendor and Product field in the Affected Product Configuration entry formatting. This powerful capability allows interesting queries to be posed of BRON. Some examples are shown in Table 1. Start in the first row, by asking about the Affected Product Configurations related to Persistence which retrieves 1,352 Affected Product Configurations. In the second row, they query BRON for the means of attacking a named vulnerability. BRON identifies 13 Techniques one of which is T1553.004 Install Root Certificate. In the third row, ask BRON about the attack patterns the technique is involved in and the tactics which an attack may be pursuing that target the browser. We see that five different tactics can target the browser, one of which is Privilege Escalation. We also discover that the browser is the vulnerability endpoint of 147 attack patterns, e.g. UDP Scan.
| Query | Results (Abbreviated) | Number of Results |
|---|---|---|
| Affected Product Configurations affected by Tactic of Persistence | Affected Product Configurations: Oracle hospitality, . . . | Affected Product Configurations: 1,352 |
| Techniques connected to CVE-2019-2432 (vulnerability in Oracle health sciences application) | Techniques: Install Root Certificate, . . . | Techniques: 13 |
| Tactics and Attack Patterns for Google Chrome (all versions) | Tactics: privilege-escalation, . . . Attack Patterns: UDP Scan, . . . |
Tactics: 5 Attack Patterns: 147 |
| Tactics and Attack Patterns for Google Chrome (version 5.0.375.0) | Tactics: privilege-escalation, . . . Attack Patterns: Buffer Overflow via Environmental Variables, . .. |
Tactics: 4 Attack Patterns: 120 |
| Tactics and Attack Patterns for Google Chrome (version 52.0.2743.82) | Tactics: NONE Attack Patterns: Overflow Binary Resource File, . . . |
Tactics: 0 Attack Patterns: 12 |
Related Sources
The sources of BRON are variously described as industry standard of common names (CVE), a list (CVE and CWE), an encyclopedia (CWE), comprehensive dictionary and classification taxonomy (CAPEC) and knowledge base (ATT&CK). Similar threat and vulnerability data within knowledge graphs and ontologies exist which offer different capabilities than those presented for BRON. This includes the STUCCO ontology and knowledge graph which incorporates information from 13 structured data sources and provides relationships among 15 entity types including software, vulnerabilities, and attacks. Another ontology, SEPSES, uses some of BRON’s sources but BRON is unique, to the authors' knowledge, in incorporating the tactics and techniques from the MITRE ATT&CK matrix and bridging them to CWE via CAPEC.
Summary
The idea behind BRON is to provide a conveniently connected graph of multiple public sources in the domain of cyber security that are already connected but challenging to traverse coherently. It supports quantitative cataloging of the composite set of cyber threat intelligence sources. The contributions of this paper are:
- BRON, a graph that stores and unifies an explicit set of security information sources while preserving the inter and intra relationships of their entries. BRON offers convenience and coherence.
- An inventory of BRON that reveals the extent of the public sources and their inter-relationships.
- A preliminary demonstration of BRON’s ability to support exploration of the information.
- Open source community code for BRON and the authors' analyses located in a GitHub repository. All code and data for the analysis are available in Python with tutorials in Jupyter notebooks.
-- Corren McCoy (@correnmccoy)


Comments
Post a Comment